- 压缩 js 命令
1 | ./node_modules/terser/bin/terser ./public/vendor/js/jockey.js --config-file ./script/terser.config.json -o jockey.min.js |
1 | terser.config.json |
1 | ./node_modules/terser/bin/terser ./public/vendor/js/jockey.js --config-file ./script/terser.config.json -o jockey.min.js |
1 | terser.config.json |
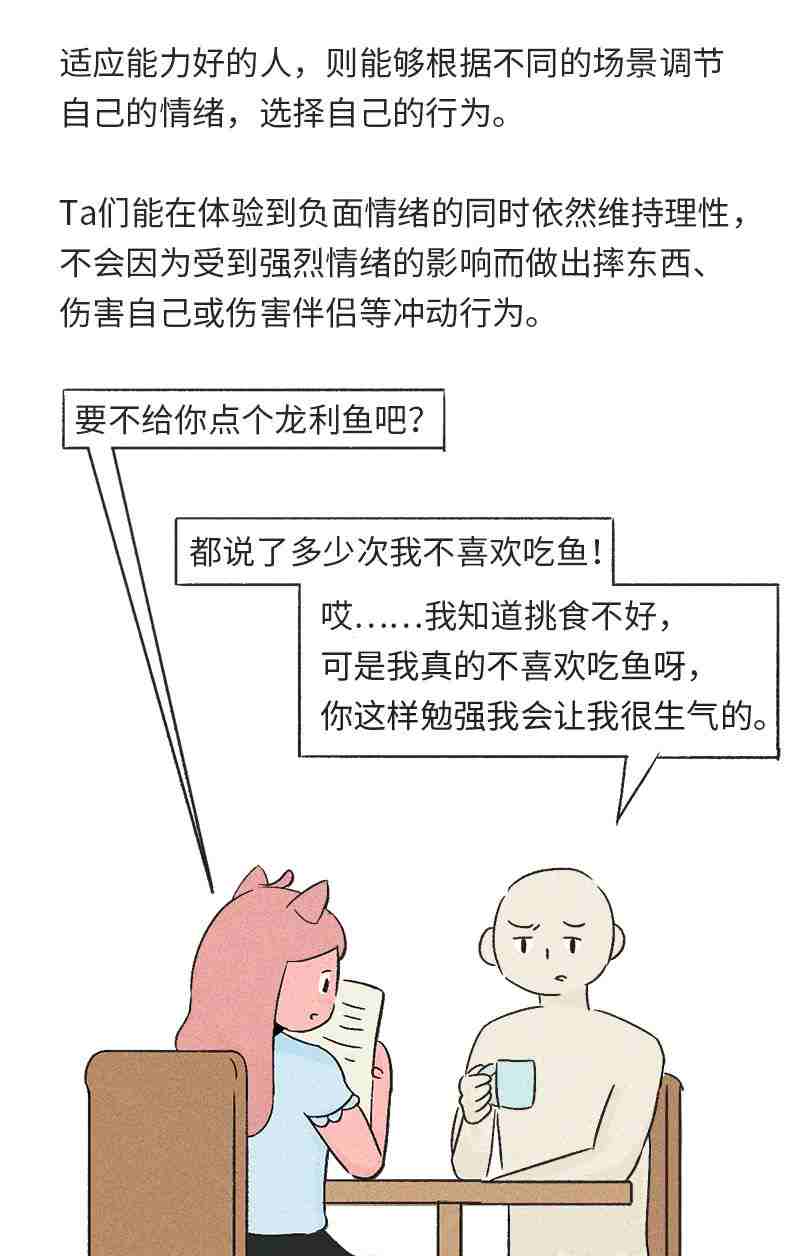
言出必行 表里如一 能够依靠 有责任感 并如实展示自己
信任是通过情感上联结建立的;情感上联结是通过情绪协调达到的
情绪协调可以用一组首字母来表示:A-T-U-N-E
关注(ATTEND)当女人需要男人的时候,请给予她们绝对的注意力。这就意味着当女人想要和你谈话时,请关掉你的游戏、放下你的手机,用行动展现出你很关心她。你要在乎她说的话,即使对你来说,她说的都是一些微不足道的事情。因为这对她非常重要,并且这意味着双方在建立情感联结。如果你在约会,请把你全部的注意力放在眼前的这个女人身上。不要四处张望,不要打量别的女人,更不要一边吃饭一边给你的好兄弟发微信。注意力代表你的感情。注意力是你表达爱的方式。转向(TUR.TOWARD)这里说的转向,并不是我们在打比方,也不是什么流行的词汇。我们要你将身体转向你的伴侣,因为在女人心目中,亲密意味着四目相对。来自新泽西州罗格斯大学(Rutger.University)的生物人类学家海伦·费希尔(Hele.Fisher)认为:“在男人心目中,亲密意味着肩并肩的工作或者玩耍。这种亲密方式也许可以追溯到史前时期。想象一下,我们的男性祖先躲藏在灌木丛后,悄悄地注视着远处,准备猎捕一头水牛。虽然他们共同面对敌人,但只是肩并肩而非面对面地战斗。”2 所以男人要牢记,除非你和你的女人准备一起猎捕水牛,那么当你和她说话的时候请你面向她。理解(UNDERSTAND)不管女人说了什么,男人要做的永远是理解。如何理解?请多多提问题。如果女人向你抱怨她的好友,你不要急着为她提供一个解决方案,不要试图分散她的注意力,不要开玩笑,不要认为你可以解决这个问题,更不要试图弱化这个问题的影响。你要询问她此时此刻的感受以及这件事对她的意义。这不仅代表你可以理解她,更说明你对她的生活有真诚的兴趣,并且你也在竭尽全力去理解那些对她来说重要的东西。当她向你抱怨她的母亲或者老板,甚至生你气的时候,请始终牢记,你的首要任务就是理解。非防御性倾听(NONDEFENSIVEL.LISTEN)如果你能够做到前面几点,即倾注你的注意力、将你的身体转向她、充分理解她,那么你就已经初步掌握了非防御性倾听的技巧。当女人批评你时,恰当地使用非防御性倾听的技巧尤为重尤为重要。不要对她的话语作出反应。没有人喜欢被批评,这会让人感到正在被攻击。但值得注意的是,如果你和她争执、辩解,她更会批评你。不要打断她的谈话。不要忘记,你的任何感受对她而言都是真实的。不管你是否同意她的观点和行为,在那一刻,她的感受都是真实的。你只需要认真倾听她的感受。为什么你有两只耳朵,却只有一张嘴巴?那是因为你花多长时间表达意见,就要多花两倍的时间来倾听。聪明的男人都会遵循这些规则。我们在爱情实验室的观察也证明了倾听十分重要。只有那些能够抑制自己的愤怒且不会有过激反应的男人,才能获得更加美好的伴侣关系。共情(EMPATHIZE)如果你是《星际迷航》的粉丝,那么请你把共情想象成瓦肯人的心灵融合。如果你认为你已经完全掌握了“理解”这一技巧,那么请你再确认一下。理解是理智上的追求,而共情是情感上的追求。不管这种感受是否符合你瓦肯人的逻辑,你都要试着去感受女人的感受。试着从她的表达中寻找线索。怎么做?你可以直接问她感觉如何。你如果能这样问,那你真是个天才。你也可以观察她的身体语言。她是否环抱双臂?抑或是呼吸急促?她的脸是不是红了?这些都意味着她很恼火。你要让她知道你重视她的感受。无论她有何种情绪都是合理的。我们并不打算从脑科学的角度深入解释这样做的原理。简单来说,当一个人感受到自己与他人联结,而非孤身一人的时候,她大脑中负责情绪处理的部分就会镇静下来。因此,重点不在于她究竟是对是错,而是你要展现出共情和怜悯的能力。高压下,男性会变得不害怕;而女性会感觉更加害怕,并对未来产生恐惧。
对于初学者来说,当女人恐惧时,请握住他的手;
更好的办法是,在一开始就帮助他避免恐惧。
P: 你们中有多少人曾经对你的生活和安全产生了恐惧?(男)
现场没有人几个人举手
P: 你上一次有这种恐惧感受是什么时候?
现场安静了一会儿。最终有人开始举手回答问题
M: 1. 上一次恐惧还是在读高中时候,他正准备和别人打架;2. 高中时,回家路上,两边都是高山,一个人独自走,感觉很恐怖;3. 大约 10 年前,喝多了酒,结果不知道走到一个治安特别差的地区,当时有点害怕,不过就那么一会儿。
(在场的每个男人并不是不好意思回答这个问题,而是他们中很多人想不起来上一次恐惧是什么时候,所有男人都追溯到很久很久)
P: 你们中有多少人曾经对生活的产生恐惧?(女)
(在场所有女性举了手)
P: 你们中有多少人在过去 6 个月对生活的产生恐惧?(女)
(在场所有女性举了手)
P: 那上个月呢?上个星期呢?(女)
(在场所有女性举了手)
P: 当你们通过酒店停车场走到培训场所的时候,有多少人感到恐惧?(女)
(每个女性依然举着手)结论:女人对恐惧的感受和男人完全不一样
在两性中,伴侣会不断的通过言语和动作向对方寻求支持和理解。当表达联结需求时,另外一个人选择划开门并走进去,也可以关上滑动门转身离开。
不去理解这些小要求的确不会把婚姻关系推入深渊。但大量没有结果或不愉快的讨论就很危险。
经年累月,一方或双方就赶到奇怪:
在“滑动门时刻”转身离开结果就是冲突升级。你注意到伴侣脸上写着“受伤”或控诉表情,你意识到自己又惹事了。如果足够幸运,你的伴侣会指出问题所在。(如上述体检事件:我想告诉你医生是怎么说的,可是你一直都在忙自己的,不能跟我好好谈谈。你知道我拿到诊断结果的时候有多紧张嘛!你他让我失望了。)
如果选择逃避并且任由伤害和愤怒发展,就是“遗憾事件”。一次冲突的爆发可能成为两个人关系史上不幸的一幕。
惹事一方如果能够道歉并承担相应责任,这个缺口就会修补。
指我们对没有完成的事情记得更清楚。
我们对那些“未完成事项”的记忆力要比对那些已完成和终止的事情的强约两倍。创伤活跃在记忆中,随时可能一遍又一遍的上演,这段回忆不断刺激,导致伴侣的消极情绪持续上升。
在两性中,如果争吵能够以双方承认错误,改正错误和加强理解而告终,那么这段争吵很快就会遗忘,换来更牢固的关系
指当信任被逐渐破坏时,人们倾向于把中性甚至是积极的事件解读为消极的含义。这导致进入糟糕盒子的次数增加。
消极诠释一旦开始,消除起来将非常困难,因为环境不是黑白分明的。
》哦,看,灯泡又灭了。
《 该死的,我又不是专职换灯泡的,你不能换嘛?(消极诠释)
其实只是表达灯泡坏了而已
》妻子看到丈夫对着窗户皱眉头,解读为不满或愤怒(消极诠释)
如果两人关系好,解读为丈夫正在为天气担心。
快乐的伴侣容易做出积极诠释,从积极的角度理解对方中性行为,而不认为对方的消极情绪是针对自己的。
四骑士是指:批评,蔑视,防御,筑墙
伴侣消极情绪越多,他们的交流就越缺乏成效。不能建设性表达出不满,他们会陷入四种消极的交流模式中,阻碍关系修复。
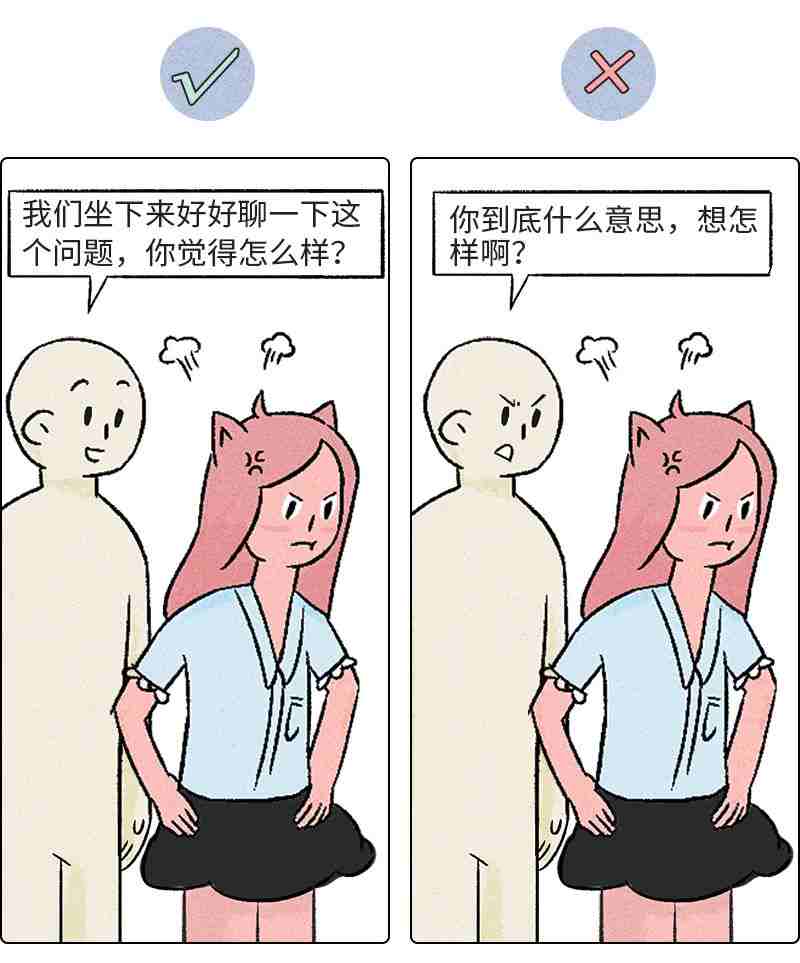
两性交往中,一些事情感到不快,就要想尽办法表达出来,不是攻击对方而是用一种温柔方式。
A: 你说过会打扫的,但桌上还是有面包屑。你说过的事情从来做不到。(总是,从来 暗示对方人格存在问题)
B: 桌上还有面包屑。我需要把他们清理干净。
A: 我告诉过你,我们需要 7 点之前到那里。你是故意磨蹭的嘛?
B: 快点,咱们晚了,现在就需要出发了。
A: 我还以为你给我买无糖冰茶了。你太自以为中心了,总是不记得我让你干什么。
B: 哦,我跟你说过偶尔带点无冰糖茶回来。
言语中暗示着你的伴侣低你一等,包括:辱骂,讽刺,嘲笑,贬低。
作为受害者,想保护自己是可以理解。防御的方式包括正常的愤怒、反击、无辜状(表现为抱怨)。
蔑视:你真够懒的。你应该把这些清理干净
防御:我找不到洗碗布,你又把他放到哪里了
蔑视:你从来没有准时过,你这回又要迟到了
防御:如果不用花那么长时间等你冲凉,我早准备好了。别唠叨了
蔑视:你没买无糖冰茶。你是怎么回事呢?
防御:喂,别怪我,是你没跟我说!
当局势最终怒不可及时,生理失控的双方就不在点头释放倾听信号(点头,眼神交流,简化音节),取而代之是无动于衷。
》我觉得,今年的感恩节咱们应该跟我爸过
《 但是我已经跟我爸妈说过了,咱们会回去的
》咱们前两年都跟你爸妈过的
《那是因为你懒得安排你那边的事情。(批评)
》我很忙。(防御)
《我就不会跟你一样,我不会坐在那儿想“我该计划计划了”,然后什么都懒得干(蔑视)。所以不要到最后一刻才告诉我去看你爸。你太自私了(批评)
》你总是这么任性(批评)。我不知道我这样努力跟你沟通有啥意义。你简直莫名奇妙。(蔑视,将视线移开,沉默)
《所以,那么。。。。你现在是想忽视我,生我闷气?
》(沉默)(筑墙)
《喂?有人在吗?出来啊!(蔑视)
使用 env 命令可以查看系统当前的环境变量。有时候我们希望能够查看一个处在运行状态的进程的环境变量。
在 Linux 系统下面,进程的环境变量信息可以通过 /proc/<pid>/environ 文件查看:
1 | $ cat /proc/<pid>/environ |
该命令的输出格式不太容易读,所有的信息挤在了同一行。使用 tr 命令将空字符替换为换行符,将会使所有的环境变量按行显示:
1 | $ cat /proc/<pid>/environ | tr \\0 \\n |
在 Mac OSX 系统下面,可以使用下面的命令,其中的 -E 选项表示打印进程的环境变量:
1 | $ ps -p <pid> -wwwE |
不过上面提到的方法并没有覆盖到所有的情况。进程的环境变量来自于两部分:进程初始化时由加载器载入的环境变量(来自于系统、父进程或者 exec 系统调用的参数);和进程执行过程中由 setenv 函数动态设置或修改的环境变量。前面的命令仅会显示第一部分的环境变量。
进程的环境变量保存在全局变量 char **__environ 中。要想显示由进程动态修改的环境变量,首先必须有这个进程的符号表,然后通过 ptrace 系统调用(比如使用 gdb)来查看。
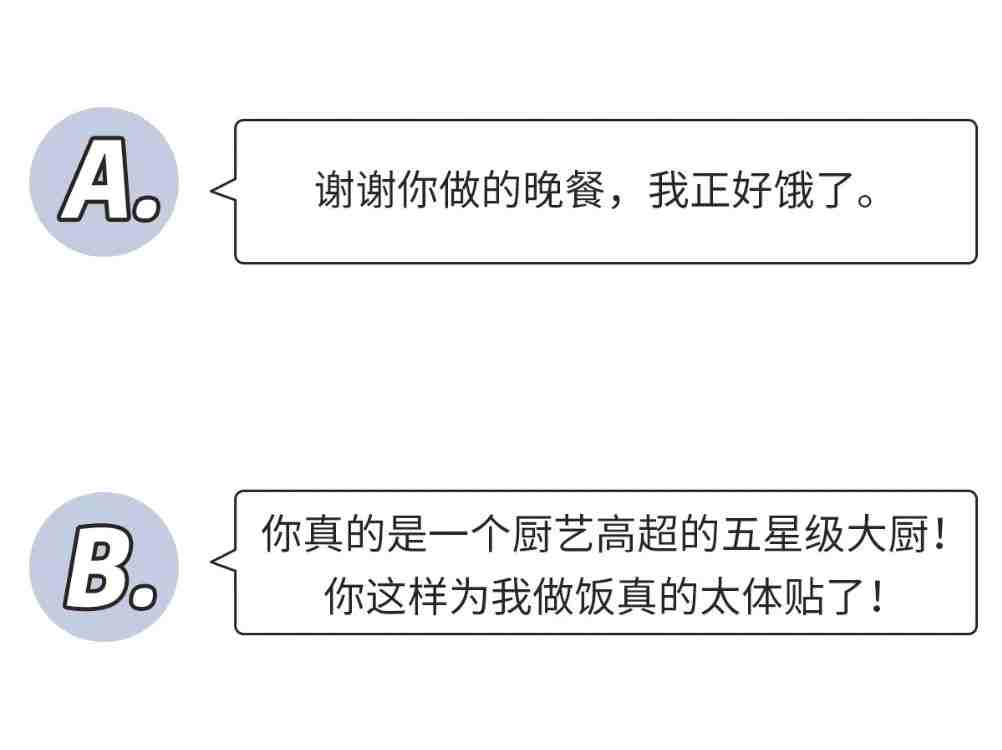
对于所有关系来说,真诚的赞美都会增强两个人之间的联结、提升亲密度
虽然说人人都喜欢被赞美,但在夸人之前,有两件事情需要我们注意。
心理学家 Fujiwara 指出,赞美寻求度(praise-seeking)是一个重要的人格维度,指的是一个人对赞美这种社会情感带来的影响的敏感性。
我们可以通过一个人面对赞美时的反应来判断 ta 是「赞美寻求度高的人」还是「赞美寻求度低的人」。
赞美寻求度高的人在任何时候都渴望得到他人的赞美,尤其是在表现不佳或心情低落时,来自他人的积极话语会让 ta 们的自尊心迅速提升(Modigliani, 1968),并对对方产生亲密感(Leary & Kowalski, 1990)。
比如,当对方为老板批评了自己而感到难过时,“我觉得你已经很棒了,你这么努力,而且其他方面老板也很认可你,我相信再多一点时间这一点你也能做到的”这类鼓励的赞美,会让 ta 们更容易重新振作起来。
相反,如果此时你试图帮 ta 解决问题,一起分析到底哪里做的不好,ta 们反而会特别悲伤或愤怒,因为这会伤到 ta 们的自尊(Kojima et al., 2003)。
所以,如果你的朋友是赞美寻求度高的人,大胆夸就完事啦!尤其在 ta 们悲伤、低落时,放下理性分析,无条件地为 ta 们摇旗呐喊,就是 ta 们最感激的事~
而对于赞美寻求度低的人来说,虽然被赞美的感觉也不错,但无论是夸奖还是批评都不会引发 ta 们太过强烈的情绪。Ta 们比较在乎的是:我做的这件事是否真的值得被人称赞,以及对方的赞美是否真诚且发自内心。
所以,如果你的朋友赞美寻求度较低,那么除了赞美 ta,对于 ta 正在烦恼的事情,ta 还会需要你帮 ta 一起分析,并给出建设性的反馈。哪怕这种建设性的反馈中包含了 ta 的不足或是缺点,只要你是基于事实并真诚地想帮助 ta,ta 都会觉得很受用。
本质上来说,奉承(flattery)是一种没有参考实际情况就给出的积极评价,不一定反映了被称赞者真实品质或能力。比如,对方明明只是一个吉他初学者,还弹错了几个音,你却一味地夸 ta 弹得很好,这样不可靠的评价,就容易让人感觉不够真诚,只是为了敷衍了事而给出的“称赞”。
** 但真诚的赞美不会脱离实际情况,无论是鼓励还是夸夸,都是基于对方真实的表现或状态给出的反馈。**
心理治疗师 Liben 认为,真诚的赞美其实并没有我们想象得那么复杂。只要在给予赞美时满足 5 个原则,对方就能充分感受到我们的真挚和诚恳。而这 5 个要素分别是:
比如:我发现你做的菜颜色搭配得特别好,美感和口感都能呈现这么好。你是怎么做到的?比如:今天听你分享的这个观点收益很多,我可能自己看书很久不一定能理解到这一层,你一说我就有醐醍灌顶的感觉。比如跟你在一起,我发现我最近也变得更加积极乐观了。成长的过程中一直会被身边的叔叔阿姨夸成熟独立,大概是因为我未成年时几次独自去夏令营、去陌生城市旅游、再独自出国读书的经历。我一直觉得这样的夸奖对我没有什么影响,但后来发现,每当我遇到困难的时候我都会用“你是个成熟独立的人,一定能够处理好这样的问题”来鼓励自己,在小团体中我因为自己的“成熟”而主动做那个领导者,在亲密关系中我也会尽可能保持自己的独立性不过度依赖对方。我把他人的夸奖内化成自己的认同,便真的成为了那个成熟且独立的人。
有时候负反馈的消失,就足以让人改变了。
我从小一直身材焦虑,被妈妈说不够瘦不好看,初中时胖过一段时间还被班里同学叫胖妞,是我很久以来的心理阴影。后来大学我出国,身边这些说我胖的声音就消失了,甚至还被 homestay 说太瘦了。后来尝试着健身,在健身房被夸底子很好,很 fit。在负反馈消失的环境里,我才慢慢正视镜子中的自己,慢慢找到属于自己的价值评判,不再被他人的言论影响。现在回国我还是没有成为“白幼瘦”,但我很喜欢我现在的身体。
说个小的吧。我帮陌生人抵着门时,有的人会非常真诚地向我表达感谢,每每听到都觉得特别开心和满足。于是我在遇到他人帮我开门时,也会非常主动且声音洪亮地说谢谢,希望帮助我的人,也能像我一样体会到帮助他人的开心。
我从小是被妈妈夸大的。刚开始的时候,我心里会有问号“为什么要夸我呢?”,后来也不知道什么时候发生了变化,像有魔法一般,我的成长轨迹就沿着妈妈夸的方向去了,妈妈夸的都成真了!
小的时候,家里特别穷,但我压根就没有自卑过。小学阶段,所有孩子放学后都要干农活,当我干得不好的时候,妈妈会说:“我女儿长大肯定不在农村,一看就不是种田的命”;当我干得好的时候,我妈妈会说:“我女儿真能干,不但学习好,还能帮妈妈干活儿”。开完家长会,妈妈会特别高兴地和我分享她坐在家长群中有多骄傲多自豪,仿佛我优秀得不得了。在转学的适应期,我妈妈逢人便夸女儿性格开朗,夸着夸着,我性格就真的变开朗了。
我今年 40 岁,去年利用空闲时间考心理治疗师,四门课过了三门,本来还挺失落的,结果我妈说:“我女儿真能干,一共四门都过了三门了,明年只考一门就行了”,瞬间就觉得这是挺高兴一事儿,晚上就出去吃饭庆祝了,今年如愿考过了剩下的一门。
曾经被业界大佬夸写作天赋,我不以为然,觉得他人的夸赞是因为没有看到真实我的。无论多少正向反馈,都无法改变“我是垃圾”的内在感觉。
后来我意识到,自己永远是内因。自尊的提升在于你是否能够发自内心地欣赏自己、共情自己。当我克服了这一点后,对他人的正面反馈也有了更多的实感。
不知道有没有人和我一样,会自己跟自己对话,自己夸自己。他人的反馈往往要等到最终成果展现出来后才能得到,但我自己可以在做好每一个小细节时,在脑中暗暗地对自己说:好棒!不管他人怎么说,哪怕最终的成果有瑕疵,但我知道自己还是在很多地方做的非常不错,所以不会丧失掉下一次努力的动力和信心。
16 岁的时候平生第一次被人夸,是一个老师,她说我有想法,有灵魂(那时正在痛苦地争取学自己热爱的专业的权利),太震惊了,记到了现在。十年过去,我仍然努力地做着那个有想法,在探索,会挣扎,会痛苦,有灵魂的我,自然也收到了更多表扬。
我的现任男朋友也是!一直夸我好看,身材好。其实我从小一直不自信,满脸痘痘,五官不好看,甚至小学还是“班丑”。但他会一直夸我,还给我拍了很多美美的照片。有时候看着照片我也会微微震惊,原来我可以这么好看。他确实让我相信,我就是很好看,谢谢他。
最近工作压力特别大,而且结果不好,得到的都是负面反馈。但同时找了一位网友学语言,网友非常耐心细致,教得专业,还会跟我分享金句。在压力下真的收获了很多正向的鼓励,感到自己的价值被认可,工作上也更有动力去做了。
读研的时候,实验不停的失败,每天都很痛苦。于是我经常去找我们的 lab manager 诉苦,跟他一起思考实验哪里出问题,跟他一起畅聊人生。有一次跟他聊到未来的规划,我说不知道要不要读博,去哪里读,也不知道考不考得上,他跟我说,“你的能力可以让你去到任何地方。你也应该去往更大的平台汲取更多的经验。不要只是停留在这里,这里对你来说不够好。” 虽然最后我还是选择留在了本校,但是他无条件的信任真的深深的激励了我,让我能够在自己的领域里安下身耕耘,让我成为了更好的自己。
今年 4 月份的时候,我在海南万宁一家民宿当义工,每天会留点大米,早上给自己炒点饭对付下。有一家三口的客人某天早餐想吃炒饭,我就给他们也做了一份,结果客人吃完特别真诚的夸这是他们吃过最好吃的炒饭,还问我是如何做的,第二天还特意买咸蛋黄回来让我继续炒。我这种炒个菜刷个碗都能被揪出一大堆毛病的人哪里见过这个,简直被彩虹屁吹晕了,瞬间中华小当家附体,恨不能一天做三顿饭来换客人一笑,对厨艺的热情也大大提升,各种食材轮换折腾了好几个月,直到再次被打击的七零八落,但确实在厨艺方面摸到了一些门道。
想来他们家的小朋友长大了一定也会像父母一样,在不经意的瞬间就可以给别人的生活带来光。我也在努力去学习,希望也能够成为给他人带去自信和热情的人。
我以前实习的时候,总是很紧张,怕自己做不好工作,也怕自己处理不好人际关系,而越是紧张就越不容易融入进集体。
直到上一份实习,领导对我很信任,我稍微做了点东西,她就会一直表扬我。有一次我请假,怕耽误工作,就在前一天晚上加班到 10 点做完了 PPT,发给她之后,她就一直在说我太棒了,但不用这样拼,好好休息也很重要。最初的我对这些赞美是手足无措的,不知道该怎样回应。但逐渐地,我开始能够打开自己,学会了与年长我很多的同事开玩笑,也越发想要努力工作去回报领导的信任。真的很感激自己能有机会在那样的神仙公司、神仙领导手下工作!
大学时玩 cosplay,cos 我最爱的动画作品《棋魂》。时隔几年,当时的室友给我发来了下面这段话:
“当时看到你出的棋魂,我是第一次被惊艳,不是你的后期、你的模仿,而是,你的内心外溢出的感情。
你喜欢一个东西,只要彻底,就会慢慢凝聚它的灵魂,也许,你本身也是它!因为每一部片子,每个角色,都是现实性格的放大化,触动你了,就产生共鸣了;喜欢上了,就融入自身了。”
这让我更清晰地认识到,自己坚定地爱着这部作品,并把其中的精神融入到自身。后来我慢慢转行,成了动画行业的人。
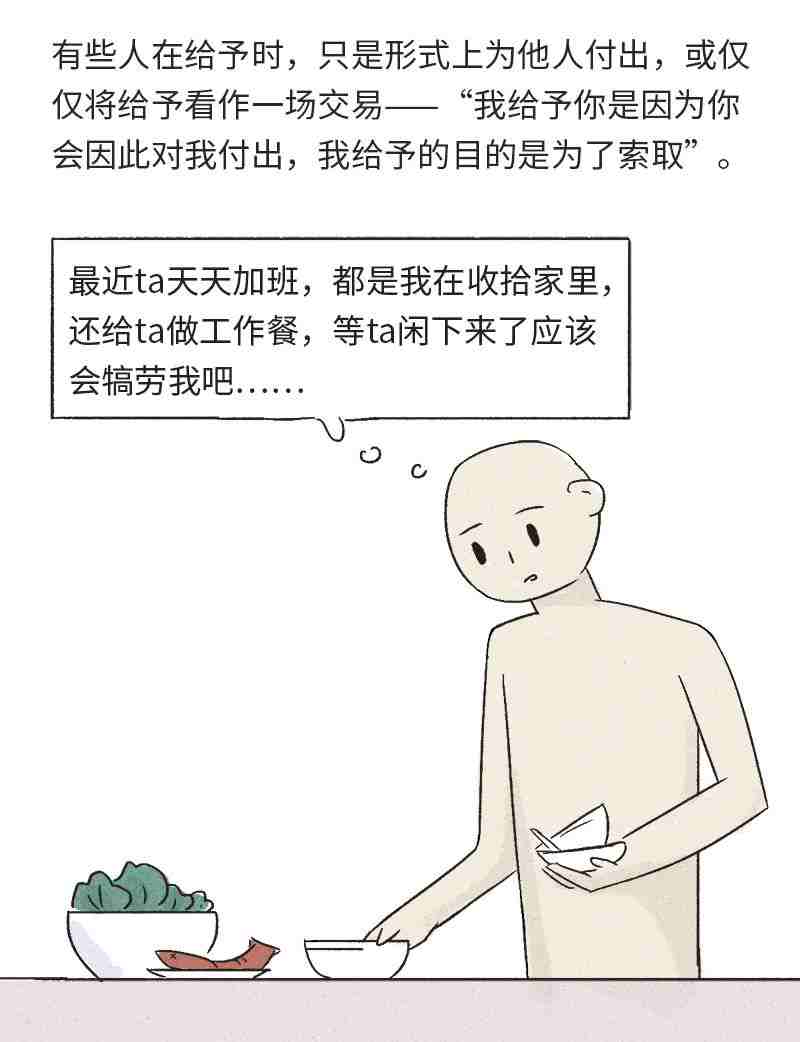
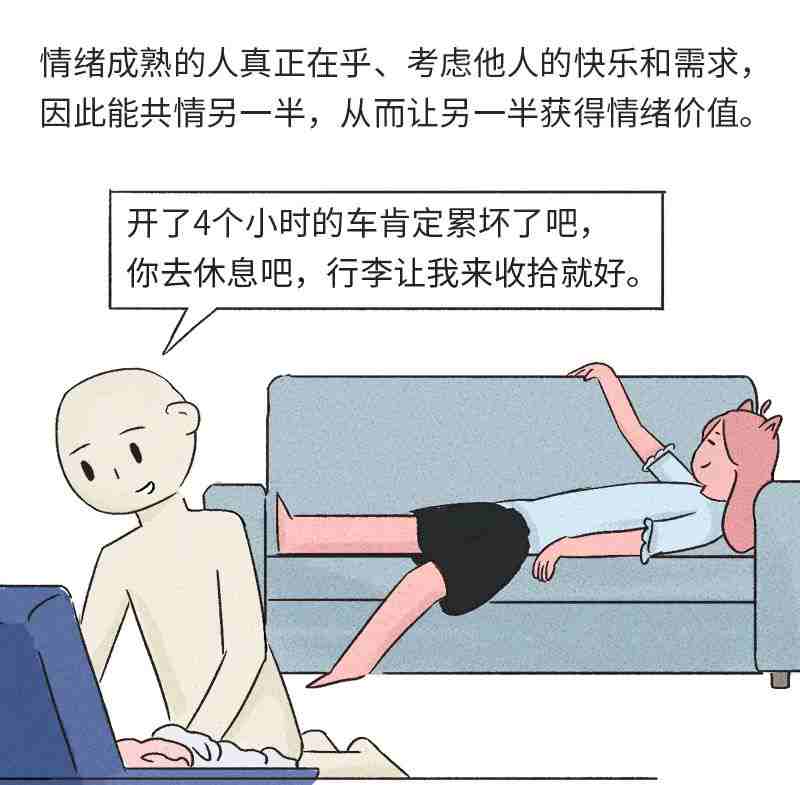
情绪价值:当一个人与伴侣相处时,ta 所感知到的情绪收益和情绪成本之差就是情绪价值。
给他人提供情绪价值的核心,在于情绪成熟






1 | { |
直接通过原始 webpack 配置是可以的;但是通过 vue 的配置就不行;怀疑是 vue 配置某个地方冲突;
通过打印配置./node_modules/@vue/cli-service/bin/vue-cli-service.js inspect > log.txt
最终测试,发现是 rule 中 vue 的配置有问题,把 cache 去掉就好,修改如下:
1 | chainWebpack: (config) => { |
配置修改之前:
1 | /* config.module.rule('vue') */ |
配置修改之后:
1 | /* config.module.rule('vue') */ |
通过iVbwQXxFy中前 4 个字符,产生加密串VwbiQVbbbQVbwwQVbVVQVwiiQVwbiQbwwQVwiVQwibQwVwQwbVQwVVQwVVQwibQwbiQwVwQwVVQwibQwVVQwbiQwbVQwViQwiwQwViQwbbQwbVQwVbQwVbQwwbQbiwQVwbiQVbibQVbiwQVbViQwViQVbVVQwVVQwbbQbiwQ。
1 |
wabc3d491 | function changeFunc(d, e, f) { |
https://www.movable-type.co.uk/scripts/tea.html